ちょっと古い cent os 7.5にVPN Serverを構築して、macから接続してみます。
iptablesでポート開放
-A INPUT -p udp -m ucp --dport 1194 -j ACCEPT -A INPUT -p tcp -m tcp --dport 9443 -j ACCEPT
udp 1194と tcp 9443を開けてみました。(443はhttps使用しているので
# systemctl reload iptables # iptables -L Chain INPUT (policy DROP) target prot opt source destination ACCEPT all -- anywhere anywhere ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT tcp -- anywhere anywhere tcp dpt:ipulse-ics flags:FIN,SYN,RST,ACK/SYN /* Accept new SSH connections. */ ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:http ACCEPT tcp -- anywhere anywhere tcp dpt:https ACCEPT udp -- anywhere anywhere udp dpt:openvpn ACCEPT tcp -- anywhere anywhere tcp dpt:tungsten-https Chain FORWARD (policy DROP) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
openvpnとtungsten-https(9443)になりました。他のでも良いけど
OpenVPNとEasy-RSAのインストール
Easy-RSAは、OpenVPNの証明書の生成ツール
yumが404エラー。。。ばかりたくさん
---> パッケージ easy-rsa.noarch 0:3.0.8-1.el7 を インストール ---> パッケージ openvpn.x86_64 0:2.4.12-1.el7 を インストール --> 依存性の処理をしています: libpkcs11-helper.so.1()(64bit) のパッケージ: openvpn-2.4.12-1.el7.x86_64 --> トランザクションの確認を実行しています。 ---> パッケージ pkcs11-helper.x86_64 0:1.11-3.el7 を インストール --> 依存性解決を終了しました。 依存性を解決しました ===================================================================================================================================================================== Package アーキテクチャー バージョン リポジトリー 容量 ===================================================================================================================================================================== インストール中: easy-rsa noarch 3.0.8-1.el7 epel 44 k openvpn x86_64 2.4.12-1.el7 epel 529 k 依存性関連でのインストールをします: pkcs11-helper x86_64 1.11-3.el7 epel 56 k トランザクションの要約 ===================================================================================================================================================================== インストール 2 パッケージ (+1 個の依存関係のパッケージ) 総ダウンロード容量: 628 k インストール容量: 1.5 M Running transaction check Running transaction test Transaction test succeeded Running transaction インストール中 : pkcs11-helper-1.11-3.el7.x86_64 1/3 インストール中 : openvpn-2.4.12-1.el7.x86_64 2/3 インストール中 : easy-rsa-3.0.8-1.el7.noarch 3/3 検証中 : easy-rsa-3.0.8-1.el7.noarch 1/3 検証中 : openvpn-2.4.12-1.el7.x86_64 2/3 検証中 : pkcs11-helper-1.11-3.el7.x86_64 3/3 インストール: easy-rsa.noarch 0:3.0.8-1.el7 openvpn.x86_64 0:2.4.12-1.el7 依存性関連をインストールしました: pkcs11-helper.x86_64 0:1.11-3.el7 完了しました!
あっさり完了
# ln -s /usr/share/easy-rsa/3.0.8 /etc/openvpn/easy-rsa
/etc/openvpn/easy-rsa # ./easyrsa init-pki init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa/pki
# ./easyrsa build-ca Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Enter New CA Key Passphrase: Re-Enter New CA Key Passphrase: Generating RSA private key, 2048 bit long modulus .....+++ ........................................................................+++ e is 65537 (0x10001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]:VPN-First CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /etc/openvpn/easy-rsa/pki/ca.crt
パスフレーズと名前を設定
pem生成
# ./easyrsa gen-dh DH parameters of size 2048 created at /etc/openvpn/easy-rsa/pki/dh.pem
サーバー証明書と秘密鍵
# ./easyrsa build-server-full server_r nopass Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key .......+++ ............................+++ writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-18753.03FthS/tmp.gjhkci' ----- Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-18753.03FthS/tmp.rCKkNq Enter pass phrase for /etc/openvpn/easy-rsa/pki/private/ca.key: Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'server_r' Certificate is to be certified until Mar 18 13:53:35 2027 GMT (825 days) Write out database with 1 new entries Data Base Updated
クライアント の証明書と秘密鍵
# ./easyrsa build-client-full client1 nopass Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key .........................................................................................................+++ ...............................................................+++ writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-18843.WcaUFr/tmp.HQESDy' ----- Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-18843.WcaUFr/tmp.xXN3Jx Enter pass phrase for /etc/openvpn/easy-rsa/pki/private/ca.key: Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'client1' Certificate is to be certified until Mar 18 13:55:42 2027 GMT (825 days) Write out database with 1 new entries
コンフィグ
[/etc/openvpn]# cp /usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf ./server_r.conf [openvpn]# vim server_r.conf
とりあえず udp 1194で動かしてみるのでそのまま
ca.crt / server.crt / server.key / dh2048.pem を変更しました。
# You can uncomment this out on # non-Windows systems. user nobody group nobody
nobodyも
# openvpn server_r.conf Fri Dec 13 23:08:28 2024 OpenVPN 2.4.12 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Mar 17 2022 Fri Dec 13 23:08:28 2024 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06 Fri Dec 13 23:08:28 2024 Diffie-Hellman initialized with 2048 bit key Fri Dec 13 23:08:28 2024 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Fri Dec 13 23:08:28 2024 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Fri Dec 13 23:08:28 2024 ROUTE_GATEWAY 140.227.119.1/255.255.255.0 IFACE=eth0 HWADDR=00:13:5d:13:06:b4 Fri Dec 13 23:08:28 2024 TUN/TAP device tun0 opened Fri Dec 13 23:08:28 2024 TUN/TAP TX queue length set to 100 Fri Dec 13 23:08:28 2024 /sbin/ip link set dev tun0 up mtu 1500 Fri Dec 13 23:08:28 2024 /sbin/ip addr add dev tun0 local 10.8.0.1 peer 10.8.0.2 Fri Dec 13 23:08:28 2024 /sbin/ip route add 10.8.0.0/24 via 10.8.0.2 Fri Dec 13 23:08:28 2024 Could not determine IPv4/IPv6 protocol. Using AF_INET Fri Dec 13 23:08:28 2024 Socket Buffers: R=[212992->212992] S=[212992->212992] Fri Dec 13 23:08:28 2024 UDPv4 link local (bound): [AF_INET][undef]:1194 Fri Dec 13 23:08:28 2024 UDPv4 link remote: [AF_UNSPEC] Fri Dec 13 23:08:28 2024 GID set to nobody Fri Dec 13 23:08:28 2024 UID set to nobody Fri Dec 13 23:08:28 2024 MULTI: multi_init called, r=256 v=256 Fri Dec 13 23:08:28 2024 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0 Fri Dec 13 23:08:28 2024 IFCONFIG POOL LIST Fri Dec 13 23:08:28 2024 Initialization Sequence Completed
動いたっぽい。
# systemctl start openvpn@server_r # systemctl enable openvpn@server_r Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server_r.service to /usr/lib/systemd/system/openvpn@.service.
動いてるっぽいです。
macから接続してみる
MacでVPN接続を設定する
https://support.apple.com/ja-jp/guide/mac-help/mchlp2963/mac
ちょっと違うっぽく openvpnに接続は
OpenVPN Connect: OpenVPN公式のクライアント
OpenVPN Connect - VPN For Your Operating System | OpenVPN
Download the official OpenVPN Connect client VPN software for your operating system, developed and maintained by our experts. Get started with our VPN software.
こちらからダウンロード 3.5.1のようで
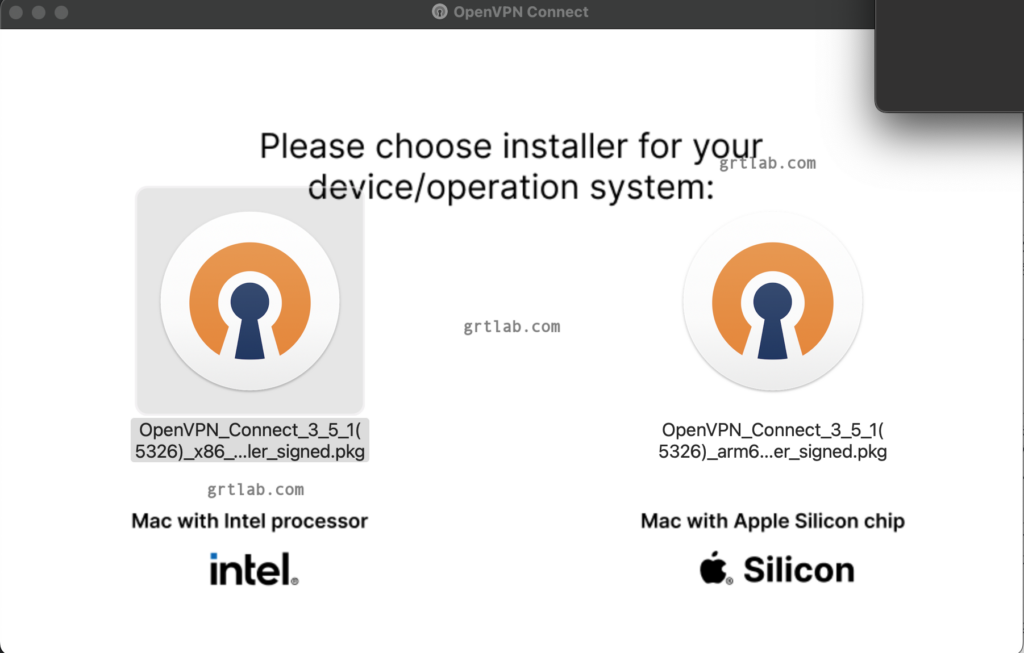
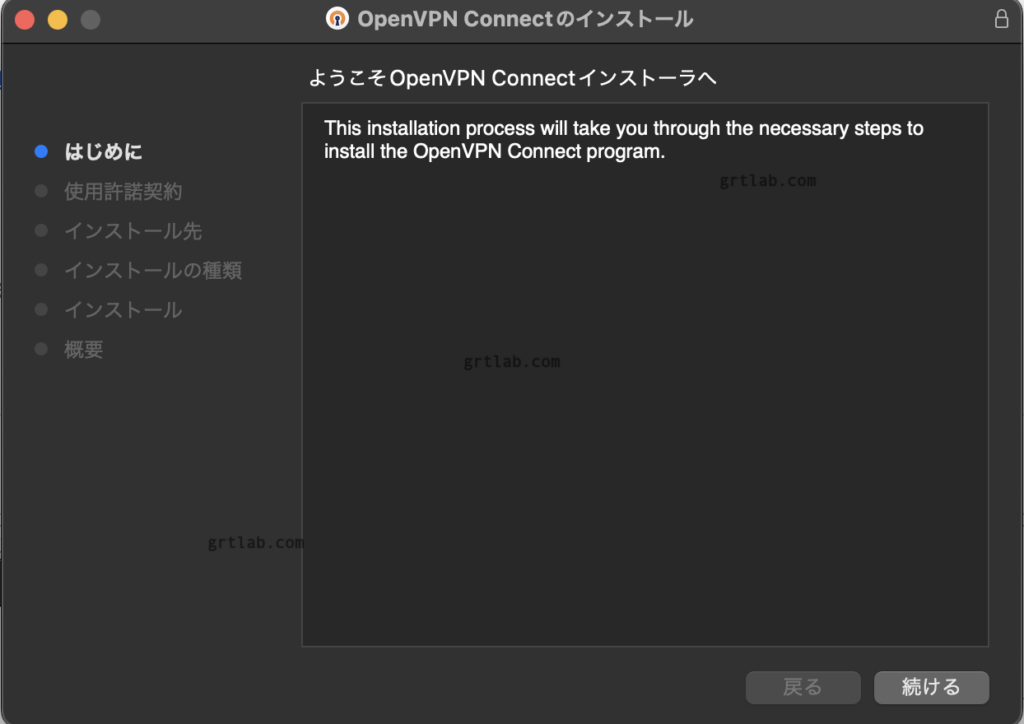

.ovpnは自分で作るらしい…
参考 https://qiita.com/SSMU3/items/bf82f76af9534b21da8c
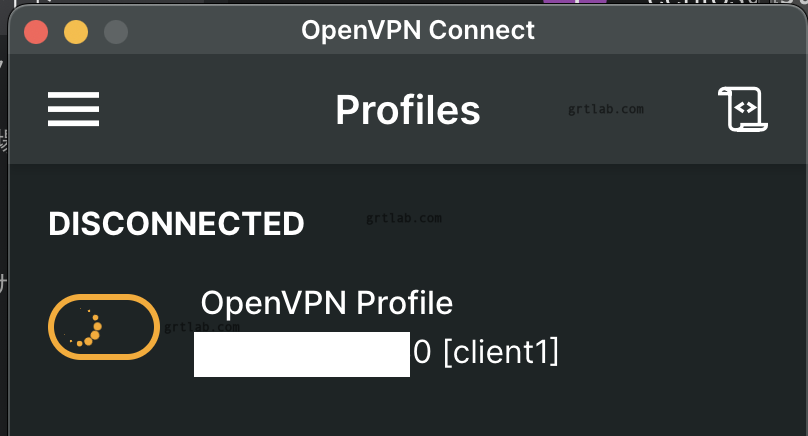
接続を試みていますが。。。今のところ接続できません!



コメント